Ecoute attentive ce jour du dernier podcast hebdomadaire de « No Limit Secu » consacré au(x) Cyber Range(s)
Parmi les invités on retrouve :
- Guillaume Prigent (Président et Co-fondateur Diateam / BlueCyForce);
- Olivier Franchi (Owner, Sysdream);
- Arnaud Kopp (Président de CyberTest System).
Ces trois spécialistes sont interrogés par les animateurs habituels Hervé Schauer, Nicolas Ruff et Johan Uloa.
Définition officielle du cyber range ?
3′ : Juste une infrastructure ?
GP : c’est pas nouveau … Très variable selon les moyens que l’on veut y mettre : copie d’un système réel dans lequel on vient s’entraîner. Champ de tir numérique ?
Histoire : 2008, idée de faire tests d’un système complet (National Cyber Range de la DARPA) au delà du simple tests « unitaires » d’équipements.
7′ : HS : les Arc-en-Ciel Team ?
AK : Au départ seulement attaque-défense entre 2 équipes (Red vs Blue) puis d’autres acteurs ont rejoint l’environnement.
Read Team : équipe d’attaquants. Soit ils ont leurs propres outils soient ils activent des générations automatiques d’attaques et de trafic.
Greeen Team : simulation de trafic légitime pour faire fonctionner le système
Yellow Team : l’équipe qui participe involontairement au scénario de l’attaquant. Ils prennent part à une activité malicieuse sans forcément s’en rendre compte.
Blue Team : elle assure la supervision, ce n’est pas seulement la défense (SOC, NOC, Réponse à incident). Elle assure le bon fonctionnement de la Blue Team => les experts ne sont pas forcément exactement en phase sur le sujet.
White Team : ils ont le contrôle de l’exercice global
Purple Team : relais d’info, legal, communication.
OF : bonne analogie entre cyber range et simulateur de vol.
17′ : Formation avant entraînement ?
OF : Le cyber range est un prolongement de la formation. La formation ce sont de petits exercices courts avant de passer en environnement complexe qui ressemble à son environnement réel.
NR : s’inquiète de la possibilité de reproduire, ne serait-ce qu’en termes de licences (ou dongles) dans l’environnement réel
GP : la formation c’est du video training + slide + labo exercice sur sa VM. Petit rappel de Confucius et du constructivisme par GP : Tout ce qu’on voit on oublie, tout ce qu’on fait, on retient ! Puis GP nous fait une petite analogie avec les Centre d’Entrainement en Zone UrBaine (CENZUB – Centre de l’armée de terre à Sissone). A ne pas confondre avec l’eunuque (SansZob) (Note du rédacteur pour vérifier si tout le mode suit). Entraînement en environnement urbain des forces.
Un cyber range c’est un environnement qui permet d’opposer des défenseurs et des opposants. Il faut qu’il y ait de la vie dans le système. Les partenaires technologiques de BlueCyForce permettent l’
NR : Concernant toujours la représentativité du système, comment fait-on pour simuler Virus Total ?
GP propose un faux Virus Total, Twitter (basé sur Mastodont), AFP … et on regénère la plateforme à chaque séquence. Malgré tout, on grille ses touches et ses backdoors à chaque jeu.
NR : Pas possible de faire du passive DNS sur 3 ans ou rapports publiques et indicateurs de compromission => on travaille en vase clos.
AK : mise en place d’un système de QuarksLab et applications de vie spécifiques
25′ NR : Quid de la qualité de scenario, qui les écrit ? (le client qui ne connaît pas ses risques ou le fournisseur qui ne connaît pas le métier)?
GP nous perd un peu… mais ajoute que c’est un peu des deux et qu’il existe à la fois une Blue Team Teachnique et une Blue Team management. Exemple : 22 pages de timeline et 32 pages de plateforme reçreçues du client. Cela dépend du niveau d’exigence du client.
NR : est-ce que vous simulez des consultants ?
GP : si c’est demandé (quand cela permet de rajouter des éléments de contexte), on le fait. Un exercice de gestion de crise, c’est une utilisation du Cyber Range. Exemple du cameraman qui intervient au milieu de la nuit …
(outre le fait de savoir à quel moment ils allaient parler de l’ENSIBS … je voulais connaître le point de vue de chacun sur le sujet et cela faisait écho à la présentation d’Eric Weber de Thales Communication and Security sur le sujet à C&ESAR 2017 : Problématique de formation des opérateurs face aux menaces Cyber : utilisation des Cyber Range )
31′ : NR : qui fait quoi avec des Cyber Range ? Quel est l’état du marché ? Formation au pentest ?
GP : Prestation d’entraînement et de formation, vente de cyber range avec +/- de prestation.
OF : on cherche à suivre les performances des joueurs. Etablir un ranking / score gobal. L’idée est que chaque année cela s’améliore
AK : ….
HS : Le Cyber Range n’est-il pas plus utile pour la défense que dans l’attaque que NR transforme en une question sur le glissement des plateformes de cyber range avec un bout d’ANSIBLE et trois clics dans le Cloud ?
GP : Au contraire les gens veulent avoir leur plateforme … même si BluecyForce a annoncé au FIC du cyber range as a service (30% des usages). Un hyperviseur avec des VMs ne font pas un CyberRange. Compliqué d’aller mettre dans le Cloud, ton routeur chiffreur de l’OTAN. Le cyber range c’est : Mon infra, mes vulns, mon chemin ! Comme au CENZUB c’est un environnement le plus réaliste possilbe pour s’entraîner à répondre aux cyber-attaques
OF : le cyber range permet de faire de la formation, de la gestion de crise mais aussi du challenge qui permet de se former en s’amusant (Coucou Malice ???)
AK : les directives telles NIS obligent à suivre des entraînement continus. Déjà le cas en zone Asie-Pacifique les entreprises critiques sont obligés d’envoyer ses salariés suivre des entraînements à l’extérieur
HS : Si on s’entraine pas régulièrement, en trois ans on a tout oublié de la formation
GP n’est pas nostalgique mais nous raconte l’évolution de son cyber range depuis SSTIC 2005 : Simulation hybride de la sécurité des systèmes d’information : « vers un environnement virtuel de formation ». SPLUNK (pseudo SIEM… so right !), QRadar, Prelude Keenaï : on ne fera pas d’entraînement pertinent à des gens s’ils n’y croient pas, s’il n’est pas représentatif. L’important c’est d’y croire. Eh Guillaume, y’a plus de carburateurs depuis longtemps 🙂
JU : Comment simule-t-on la pression psychologique de la crise ?
GP nous met en garde sur la multiplicité des Teams mais le besoin d’avoir une équipe d’acteurs crédibles
NR : simuler une équipe de l’ANSSI qui débarque c’est possible ?
Mot de la fin :
49′ HS : l’entrainement c’est ce qui fait le succès de ce qu’on a enseigné au départ. La formation c’est bien, l’entrainement c’est mieux. Teddy Riner s’entraine tous les jours
(outre le fait de savoir à quel moment ils allaient parler de l’ENSIBS … je voulais connaître le point de vue de chacun sur le sujet et cela faisait écho à la présentation d’Eric Weber de Thales Communication and Security sur le sujet à C&ESAR 2017 : Problématique de formation des opérateurs face aux menaces Cyber : utilisation des Cyber Range)
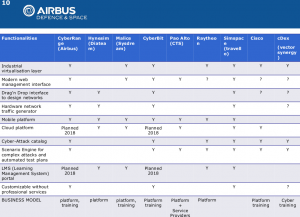
en goody : Un bon doc d’Airbus DS sur le sujet.