Writing Nexpose Vulnerability Checks will soon hurt you …
So, if you need some help, I’m your guy 😉
Thanks to Rapid7 community for the basics. Let’s see how to set it up in four steps.
step 1 : write locally with your own text editor 2 files (vulnerability desccriptor = .xml file & vulnerability check = .vck file)
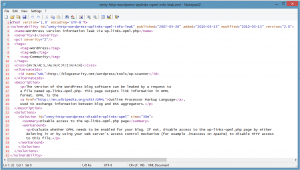
Vulnerablity descriptor file contains any information about your specific vulnerability (title, description, severity, CVE IDs, CVSS score, etc.).
You may have several vulnerability check files containing multiple tests which are compiled at runtime and used by Nexpose to verify the existence (or non-existence) of your vulnerability described in the descriptor.
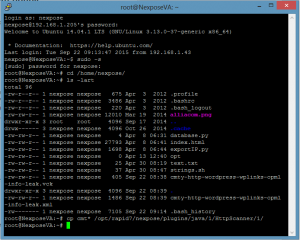
step 2 : put the files in Nexpose files system
Depending upon your system, you may juste have to pscp the files with Putty client
As it’s always a pitty to remember those commands, I just give it to you in plain text below so you’ll just have to copy/paste
C:\Program Files (x86)\PuTTY>pscp « c:\logs\nexpose\cmty-http-wordpress-wplinks-opml-info-leak.vck » nexpose@192.168.1.205:/home/nexpose
nexpose@192.168.1.205’s password:
cmty-http-wordpress-wplin | 0 kB | 0.4 kB/s | ETA: 00:00:00 | 100%
C:\Program Files (x86)\PuTTY>pscp « c:\logs\nexpose\cmty-http-wordpress-wplinks-opml-info-leak.xml » nexpose@192.168.1.205:/home/nexpose
nexpose@192.168.1.205’s password:
cmty-http-wordpress-wplin | 1 kB | 1.5 kB/s | ETA: 00:00:00 | 100%
step 3 : deploy this vulnerability check into Nexpose by simply copying your .xml and corresponding .vck file into the following directory:
/opt/rapid7/nexpose/plugins/java/1/HttpScanner/1/
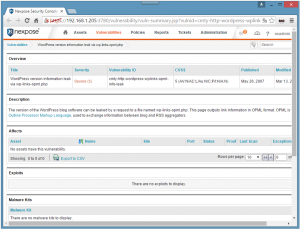
step 4 : restart your Nexpose Security Console and browse to your brand new vulnerability
Download vulnerability descriptor file
Download vulnerability check file
Notes: I just wrote this post as a proof of concept for one of my customers.
It’s always funny when you want to write a post to discover that you can’t do it the simple way you dream of it : impossible to upload xml/vck file, outdated filezilla client you have to upgrade, WordPress formatting nightmare …


Great job, Laurent !