Le sujet :
Voir page Wikipedia FR ou mieux Wikipedia EN
Raccourci :
Un vulgarisation du sujet grâce à une vidéo de 5mn de Romain du Marais
Les faits : « In an operation that cybersecurity experts have described as exceedingly sophisticated and hard to detect, the hackers installed malicious code in updates to SolarWinds’s widely used Orion software, which was sent to as many as 18,000 customers.
The malicious code provided the hackers access to the customers’ computer networks and, as clients around the world continue to comb their systems for signs of the Russian hackers, the list of victims is expected to grow. »
Chronologie :
Octobre 2019 : premiers essais à blanc de la méthode de distribution du malware
Mars 2020 : distribution de la backdoor
8 décembre 2020 : FireEye, par le biais d’un article de blog de son CEO Kevin Mandia communique sur le hack dont elle vient d’être victime avec pour conséquence le vol d’une partie des outils utilisés par ses Red Teams.
Reuters et les agences de presse généralistes relaient l’information : U.S. cybersecurity firm FireEye discloses breach, theft of internal hacking tools
13 décembre 2020 : communication coordonnée de FireEye, solarwinds, Microsoft et du gouvernement américain.
Premiers détails:
NextImpact – 23 décembre 2020
Piratage de SolarWinds : un ancien salarié avait alerté, en vain
D’après le très bon article original de Bloomberg du
SolarWinds Adviser Warned of Lax Security Years Before Hack by Ryan Gallagher
Communication de crise : SolarWinds spokesperson said in a statement, “Our top priority is our work with our customers, our industry partners and government agencies to determine whether a foreign government orchestrated this attack, best understand its full scope, and to help address any customer needs that develop. We are doing this work as quickly and transparently as possible. There will be plenty of time to look back and we plan to do that in a similarly transparent way.”
In addition, the company said it is collaborating with law enforcement and “will continue gathering all relevant information to ensure an incident like this does not happen again.
Les acteurs :
Kevin Thompson, solarwinds’s chief executive officer, former securty adviser at solarwid
Ian Thornton-Trump, chief information security officer at threat intelligence firm Cyjax Ltd
Tim Brown former chief technology officer at Dell Security, current vice president of security architecture
Vinoth Kumar Cybersecurity expert who discovered FTP server credential on gitHub
Former internal langue de pute, ex solarwind : A former SolarWinds employee, who worked as a software engineer at one of the company’s U.S. offices, said SolarWinds appeared to prioritize the development of new software products over internal cybersecurity defenses.
Jake Williams, aka monsieur-je-sais-tout, a former hacker for the U.S. National Security Agency who is now president of cybersecurity firm Rendition Infosec, said technology companies such as SolarWinds that build and produce computer code often “don’t do security well.”
Les victimes :
At Least 200 Victims Identified in Suspected Russian Hacking, dont :
- FireEye
- U.S. Department of the Treasury
- U.S. National Telecommunications and Information Administration (NTIA)
- U.S. Department of State
- The National Institutes of Health (NIH) (Part of the U.S. Department of Health)
- U.S. Department of Homeland Security (DHS)
- U.S. Department of Energy (DOE)
- U.S. National Nuclear Security Administration (NNSA)
- Some US states (Specific states are undisclosed)
- Microsoft
- Cisco
Les affreux :
Alors, Dark Halo ou bien APT29 (aka Cozy Bear), un groupe de hackers lié au SVR (Служба внешней разведки Российской Федерации, retranscrit en Sloujba vnechneï razvedki Rossiskoï Federatsi2 – Service des renseignements extérieurs de la fédération de Russie – Russian Foreign Intelligence Service) ?
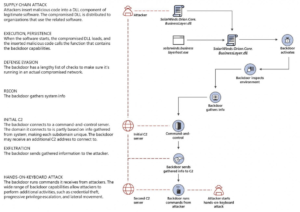
Un peu de technique :
Très bon article intégrant pas mal de détails techniques compréhensibles par ma mère sur l’attaque dans l’article The SolarWinds cyberattack: The hack, the victims, and what we know
Pour aller, plus loin : le technical write-up de Microsoft
Conclusion de Costin Raiu (Kaspersky GREAT) :
Even if SolarWinds had robust cybersecurity practices, however, it might not have deterred the alleged Russian hackers, who U.S. authorities described as highly skilled, patient and well resourced, demonstrating “complex tradecraft” in their attacks.
“The reality is that sophisticated threat actors, no matter how good the defenses, will eventually succeed,” said Costin Raiu, director of global research and analysis at the cybersecurity firm Kaspersky. “If the cost justifies the effort, the breach will happen.”
Mises à jour :
02/01/2020 : The New-York Times : As Understanding of Russian Hacking Grows, So Does Alarm
04/01/2020 : Detecting Supernova Malware using Splunk
05/01/2020 : SolarWinds Hit with Securities Class Action Over Statements in Run-Up to Cyberattack on Fed. Government
05/01/2020 : FBI, CISA, NSA Officially Blame Russia for SolarWinds Cyber Attack